Many mid to large corporations today have environments which consist of both on-premises and SaaS solutions that are constantly growing in number. These companies may also utilize one or more cloud providers. Managing identities across this diverse landscape can be challenging in the absence of a suitable IAM platform. Consider the effort to:
- Create identities for each user across these applications
- Discover all the accounts that need to be disabled when a person leaves the firm
- Discover all the accounts and entitlements that a person has to support periodic access reviews
Additionally, there is the risk related to not disabling these accounts in a timely manner; how many orphaned accounts are there in the environment today?
At some of our multi-national customers, this landscape increases in complexity as some applications are only available to regional users and others are available to the global user community. The challenges related to globally distributed companies will be explored in detail in an upcoming post.
Aside from the complexity and high cost of managing this diverse landscape, there are additional requirements to enforce security and comply with regulatory mandates. The need for governance has never been higher and traditional IAM solutions were not designed to meet the challenges imposed by this type of environment.
OpenIAM has been helping companies solve these challenges for years by delivering a unified, feature complete IAM platform which has the flexibility to be adapted to each customer’s varying business requirements.
Identity governance functionality
OpenIAM provides a comprehensive set of Identity Governance & Administration (IGA) features that enable control as well as reduce the time and effort needed to manage identities across connected systems. To ensure that users only have access to what they need, OpenIAM provides functionality to:
- Automate user provisioning/deprovisioning with integration to one or more authoritative sources and downstream systems
- Manage roles and entitlements
- Manage birthright access using a business rules engine
- Control the flow of execution using a workflow engine
The automated lifecycle functionality is complemented by a self-service portal which empowers end-users by allowing them to:
- Manage their own profile
- Change/reset their password
- View their own access. If they have direct reports, they can view their subordinates’ access as well.
- Request access from a service catalog using a shopping cart paradigm. Requests can be integrated with workflows. All access request workflows in OpenIAM support “n” levels of approval with support for service level agreements and escalations.
To fulfill regulatory requirements, access certification is provided. Access certification contains functionality to:
- Collect evidence of a user’s access across applications
- Review access using a streamlined interface
- Administer the certification campaign via tools which include a progress dashboard and UI functionality which enables delegation to another reviewer, cancellations, and sending notifications.
The OpenIAM Governance platform is described in detail on our Workforce Identity Overview page.
Architecture
The functionality described above is the result of the functionality found in the service layer and integration options enabled by the flexible deployment architecture.
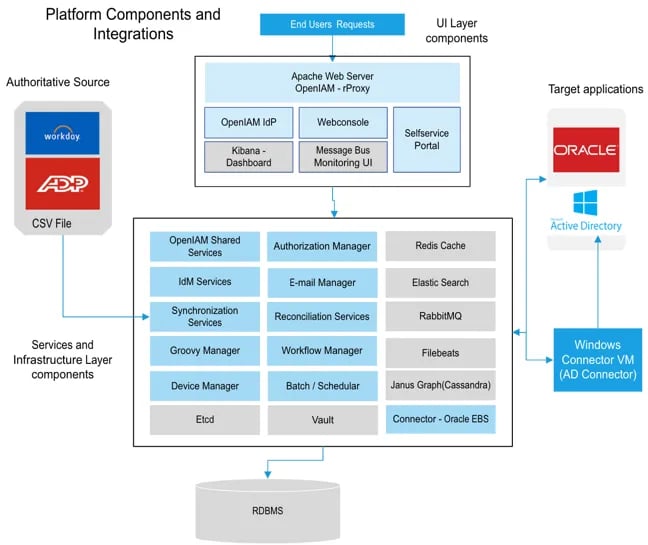
In the diagram above, the services are grouped into categories such as Shared Services and IDM Services. Each category may contain several services. These services may utilize infrastructure services like Vault, where secrets are maintained, or Redis, which is a distributed in-memory cache. Communication between the services is performed through RabbitMQ. Besides decoupling the services, the message bus also allows for services, especially the connectors, to be moved around. Consider the following scenario where OpenIAM is deployed at a cloud service provider but needs to integrate with both cloud and on-premise applications.
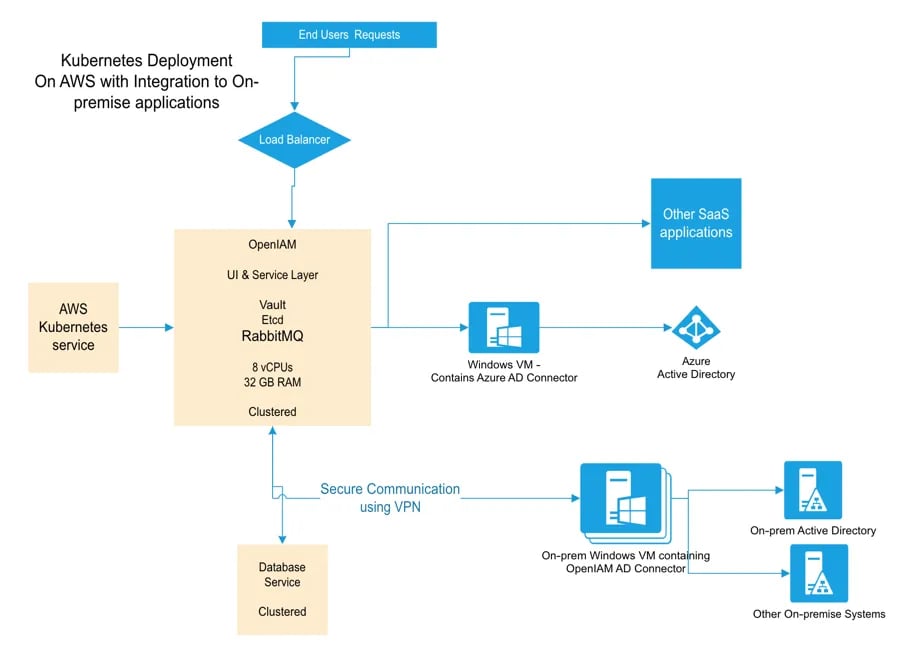 Sample deployment architecture using Kubernetes on AWS
Sample deployment architecture using Kubernetes on AWS
The diagram above shows that connectors which need to integrate with on-premise systems are deployed on-premise in a “connector VM”. Each of the connectors in the VM communicate with OpenIAM in the cloud through the message bus. As a result of this model, only one (1) IP address and one (1) port need to be opened regardless of the IP and port requirements of the end application. This communication is further protected over a VPN.
In this example, OpenIAM is already in the cloud and no special access is required to integrate with SaaS applications.
Conclusion
As highlighted above, OpenIAM provides rich business and technical functionality to allow integration with applications regardless of whether they are in the cloud or located on-premise.